BGP Lab: Cisco and Juniper Interoperability
Blog post description.
9/18/20244 min read
Introduction
This lab explores the configuration and operation of Border Gateway Protocol (BGP) in a multi-vendor environment using both Cisco and Juniper routers. BGP is a path vector protocol that is essential for routing between different autonomous systems (ASes) in large-scale networks, such as the Internet. In this lab, BGP is used to manage routing information between two distinct ASes: AS 100 and AS 200.
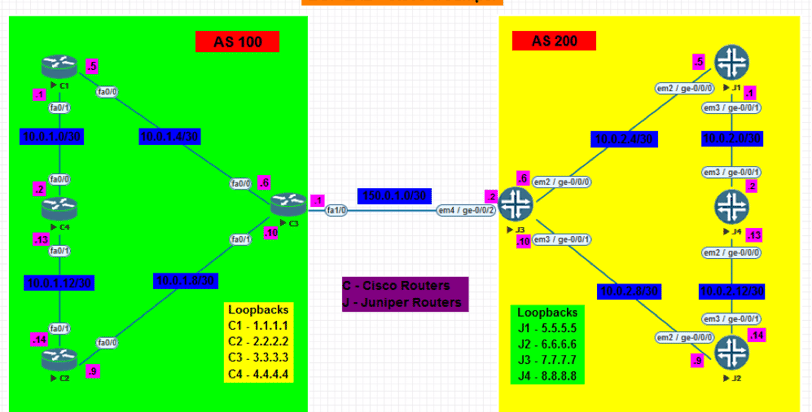
Network Topology Overview
The lab is divided into two autonomous systems, each containing both Cisco and Juniper routers. The focus of this lab is on configuring and verifying BGP sessions between routers within and across these ASes.
- Autonomous System (AS) 100:
- Routers: C1, C2, C3, C4
- Loopback Addresses:
- C1: 1.1.1.1
- C2: 2.2.2.2
- C3: 3.3.3.3
- C4: 4.4.4.4
- AS 100 handles routing within the green area of the topology. Routers in this AS will exchange BGP routing information and establish peerings with routers in AS 200 through eBGP (external BGP).
- Autonomous System (AS) 200:
- Routers: J1, J2, J3, J4
- Loopback Addresses:
- J1: 5.5.5.5
- J2: 6.6.6.6
- J3: 7.7.7.7
- J4: 8.8.8.8
- This AS handles routing in the yellow section of the topology. Similar to AS 100, routers in AS 200 will establish iBGP sessions within the AS and eBGP sessions across AS boundaries.
- Inter-AS Connectivity:
- Routers C2 (Cisco) and J2 (Juniper) will act as the eBGP peers between AS 100 and AS 200.
- Subnet: 192.168.10.0/30 connects the border routers C2 and J2.
The BGP lab demonstrates how routers in different autonomous systems can share routing information, ensuring that networks in different ASes can communicate.
Router Details
Here are the routers used in the setup and their corresponding loopback addresses:
- AS 100:
- C1: Cisco Router with loopback 1.1.1.1
- C2: Cisco Router with loopback 2.2.2.2
- C3: Cisco Router with loopback 3.3.3.3
- C4: Cisco Router with loopback 4.4.4.4
- AS 200:
- J1: Juniper Router with loopback 5.5.5.5
- J2: Juniper Router with loopback 6.6.6.6
- J3: Juniper Router with loopback 7.7.7.7
- J4: Juniper Router with loopback 8.8.8.8
BGP Configuration Details
This lab involves configuring BGP on both Cisco and Juniper routers, establishing iBGP (Internal BGP) sessions within each AS and eBGP (External BGP) sessions between routers in different ASes.
BGP on Cisco Routers (AS 100)
Sample configuration for C1 (iBGP):
```bash
Router(config)# router bgp 100
Router(config-router)# neighbor 192.168.1.2 remote-as 100
Router(config-router)# neighbor 192.168.1.2 update-source loopback 0
Router(config-router)# network 1.1.1.1 mask 255.255.255.255
```
In this configuration:
- Router C1 is configured in AS 100.
- It establishes an iBGP session with C2, advertising its loopback (1.1.1.1/32).
- The update-source command ensures that loopback interfaces are used for peering.
Sample configuration for C2 (eBGP):
```bash
Router(config)# router bgp 100
Router(config-router)# neighbor 192.168.10.2 remote-as 200
Router(config-router)# network 2.2.2.2 mask 255.255.255.255
```
C2 establishes an eBGP session with J2 in AS 200 via the 192.168.10.0/30 subnet, advertising its loopback (2.2.2.2/32).
BGP on Juniper Routers (AS 200)
Juniper routers follow a similar configuration syntax with their Junos OS.
Sample configuration for J1 (iBGP):
```bash
set routing-options autonomous-system 200
set protocols bgp group ibgp type internal
set protocols bgp group ibgp neighbor 192.168.1.2 peer-as 200
set protocols bgp group ibgp local-address 5.5.5.5
``
J1 is configured for iBGP within AS 200, establishing a session with its internal peers using the loopback interface as the source.
Sample configuration for J2 (eBGP):
```bash
set routing-options autonomous-system 200
set protocols bgp group ebgp type external
set protocols bgp group ebgp neighbor 192.168.10.1 peer-as 100
set protocols bgp group ebgp local-address 6.6.6.6
```
J2 establishes an eBGP session with C2 from AS 100, exchanging routing information between the two autonomous systems.
Key BGP Features Observed
1. iBGP Sessions:
Routers within each AS use iBGP sessions to ensure full routing information exchange within the autonomous system. This ensures that all routers in the AS are aware of each other’s loopback addresses and connected networks.
2. eBGP Sessions:
The primary feature of this lab is the configuration of eBGP between AS 100 and AS 200. Routers C2 and J2 establish a BGP session over the 192.168.10.0/30 subnet. This allows routing information to be exchanged between the two autonomous systems, facilitating inter-AS communication.
3. BGP Route Advertisement:
Loopback networks in each AS are advertised via BGP, with each router advertising its own loopback network as a /32 route. BGP's path selection process ensures that the best route to each network is chosen based on AS path, next hop, and other attributes.
4. BGP Peering:
Proper BGP peering was established between all iBGP and eBGP peers, ensuring that routes were propagated correctly within and across AS boundaries.
Verification and Testing
Cisco Verification Commands
To verify BGP neighbors on Cisco routers, the following command was used:
```bash
show ip bgp summary
```
This command shows the BGP neighbor status, confirming that iBGP sessions are established between Cisco routers within AS 100, and the eBGP session between C2 and J2 is active.
```bash
show ip bgp
```
This command displays the BGP routing table, which includes routes learned from other BGP peers. For example, C1 will have routes learned from C2, which in turn learned routes from AS 200.
Juniper Verification Commands
On Juniper routers, the following command was used to verify BGP peering:
```bash
show bgp neighbor
```
This command provides detailed information about BGP neighbors, showing whether the session is established and the status of the routes exchanged.
Additionally, the command:
```bash
show route protocol bgp
```
was used to view BGP-learned routes in the Juniper routing table, verifying that loopback addresses and external networks were properly advertised and received.
Conclusion
This BGP lab successfully demonstrated the configuration of BGP in a multi-vendor environment, with routers from both Cisco and Juniper participating in iBGP and eBGP sessions. By establishing neighbor relationships both within and across autonomous systems, this lab replicates real-world BGP deployment scenarios where multiple organizations or divisions exchange routing information over the internet or private networks.
Next Steps
Future enhancements could include:
- Route Reflectors: Implementing a route reflector in each AS to reduce the full mesh requirement of iBGP.
- BGP Attributes: Experimenting with BGP attributes like MED (Multi-Exit Discriminator) or Local Preference to influence path selection.
- BGP Security: Enabling BGP authentication to secure BGP sessions against unauthorized updates.
